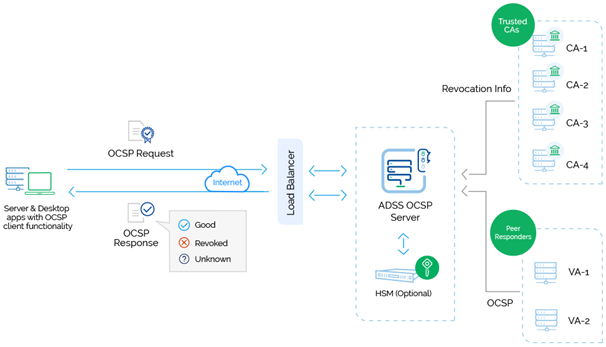
OCSP stands for Online Certificate Status Protocol and is used by Certificate Authorities to check the revocation status of an X.509 digital certificate.
In this blog we answer some of the most common questions about OCSP including how it works, the roles of certificate authorities and certificate validation authorities, and how to check certificates via a CRL.

How does OCSP Work?
When a user requests the validity of a certificate, an OCSP request is sent to an OCSP Responder. This checks the specific certificate with a trusted certificate authority and an OCSP response is sent back with a response of either ‘good’, ‘revoked’ or ‘unknown’.
What is a Certificate Authority and how do they work?
Certificate Authorities (CA) are a core part of a digital trust infrastructure that issues and manages digital certificates which can be used to verify the identity of public key subjects.
Certification Authorities are deployed as part of an organisation’s IT security architecture and operated by internal security teams or are operated by Trust Service Providers (TSPs). Certificate Authorities use the Public Key Infrastructure (PKI) X.509 certificate to verify whether public keys match the identity of the user.
The digital certificates contain:
- The owner’s name
- The owner’s public key
- The issuing CA’s name
- Certificate Validity Dates (valid from, valid to)
- Additional optional information (e.g. what the certificate can be used for, where to check the revocation status of the certificates, etc.)
Certificate Authorities digitally sign the above data to prevent further modification. CAs use their private key to sign digital certificates and anyone with the CA’s public key can verify the signature on a digital certificate, trusting the information as it cannot be modified.
Proof of the signer’s identity is vital so in order to obtain a digital certificate from a Certificate Authority you are required to provide proof of identity, either face-to-face or via online background checks, before a certificate can be issued.
In the EU, eIDAS certified CAs are known as Qualified Certificate Authorities and are operated by Qualified Trust Service Providers (QTSPs).
What is a certificate validation authority?
Ascertia’s ADSS OCSP Server is an advanced x.509 certificate Validation Authority server that conforms to the IETF RFC 6960 standard, is FIPS 201 Certified (APL #1411), and approved for use by US federal agencies for HSPD-12 implementations.
The ADSS OCSP Server is a robust validation hub solution capable of providing OCSP certificate validation services for multiple Certificate Authorities (CAs) concurrently.
Simple or sophisticated validation policies are supported for each individual CA and ADSS OCSP Server provides a detailed historical record of all transactions together with an easy to use OCSP request and response viewer.
This is essential for billing and/or troubleshooting within managed service infrastructures or enterprise systems.
How can I check my CRL certificate?
CRL stands for Certificate Revocation List. CRLs contain a list of revoked digital certificates from certificate authorities.
Certificates can be revoked for a number of reasons – someone may have reported their smartcard or USB token as lost, a signer could have left the company and is no longer authorised to sign, or the certificate could have been compromised. Digital certificates on a CRL should no longer be trusted.
CRLs provide a method of confirming the status of digital certificates by adding certificate serial numbers to a list that is signed and maintained by a Certification Authority. These lists grow in larger deployments and take time for clients to download when checking revocation.
OCSP offers greater efficiencies over CRLs for larger deployments. OCSP servers consume CRLs in order to provide an indication of whether the certificate was revoked - in this model the OCSP must refresh the CRL on a schedule to ensure it is providing up to date revocation information.
Advanced OCSP products provide the ability for the OCSP to query a CA’s database directly. This provides real-time revocation and certificate whitelisting. Certificate whitelisting provides additional assurance to end entities and confirms that the CA actually issued the certificate.
In comparison to CRL checking, OCSP requests contain far less data so are easier for networks to handle as systems do not have to download the latest list of every revoked signature whenever a certificate is checked.
Contact Us to discuss your requirements and learn more about how our solutions can be used to provide OCSP certificate validation services.