Does your business require digital signatures to be verifiable months, years or even decades later? In this blog, we discuss long-term signatures and what you should look for when choosing a provider.
It is clear that digital signatures are a very valuable security technique that enables data integrity (proving that the information has not changed since signing) and user authentication (proving who signed-off or approved the information).
Digital signatures are now widely used in various industries and applications from signing of machine-readable travel documents (MRTDs) to payment transactions to e-invoicing.
Digital signatures
For many business applications, the use of a basic digital signature is sufficient since they are only relied upon in real-time as part of one session. An example of this is user authentication as part of access to websites or other online resources.
For important business documents that need to be verifiable for several months or years, a basic signature is not enough. Basic digital signatures are only shown as valid for the lifetime of the certificate typically only one or two years.
How does a revoked or expired certificate effect digital signatures?
So, what will happen to documents that were already signed by users whilst their certificates were valid - can these still be verified in the future?
The simple answer is “no”. The signatures can no longer be trusted because the signer’s digital certificate cannot be validated once they are expired. A signature applied two weeks before certificate expiry will not be shown as trusted on the 15th day. So, be careful about using basic signatures to sign important long-term documents!!
The central issue is that the digital signature should not be verified based on current time but rather at the time the document was actually signed.
The simple way to do this is to check that the signer’s certificate was valid (not expired or revoked or out-of date) at the time of signing. If the certificate was valid at the time of signing, then the signature holds, no matter if later certificate expires or is revoked.
However, the problem with this strategy is independently proving when the document was signed.
You cannot simply rely on what the signer states as the time of signing. To overcome the problem of verifying signatures after a few months or years requires the basic signature to be enhanced to what is called a long-term digital signature.
How are long-term signatures created?
The process of creating long-term signatures is as follows:


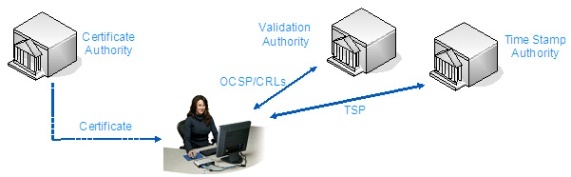
When the user signs a document, the digital signature application also requests and embeds within their signature a secure timestamp from a trusted Time Stamp Authority (TSA).
The timestamp returned by the TSA is digitally signed by the TSA so that it can be independently authenticated and trusted. It is also linked to the original signed document so it cannot be used with any other document. The embedded timestamp provides independent proof of the time of signing.
The digital signature application contacts the appropriate Validation Authority (VA) to retrieve the certificate status for the signer’s certificate.
The certificate status information (using either signed CRLs or OCSP responses) is provided by the VA. It provides an authoritative view on whether the certificate is currently trusted.
OCSP is the preferred method for this process as it is only a few KB in size and does not bloat the signature. The signer’s digital signature application also embeds this certificate status information inside the signature for future verification by anyone.
Now this signature with an embedded timestamp and certificate status information is referred to as a long-term digital signature.
Anyone can check such signatures without having to contact an online trusted authority. They can see what time the signature was applied and also what the signer's certificate status was at the time of signing. It does not matter if the certificate is later revoked or naturally expires. The original digital signature still holds since its status was verified at the time of signing.
Ascertia uses such long-term signatures on its PDF datasheets and solution sheets. Anyone with the widely distributed Adobe Reader product can view the PDF and see the signature (and embedded timestamp and certificate status information).
Since we use a certified signature type, no one can change the content of the document without breaking the digital signature. Our documents remain fully trusted to the life of the CA - currently until 2023!
Long-term signature formats
There are many standard specifications and profiles for long-term signatures. Ascertia is a world leader in supporting all popular signature formats within its server, desktop and applet products, including:
- PAdES - PDF long-term signature
- XAdES - XML long-term signatue
- CAdES - CMS-based long-term signature
See the relevant PDF and ETSI specifications if you require more information on these standard formats.
Enhancing basic signatures to long-term signatures
In the description above, the signer creates the long-term signature at the time of signing a document. This is not the only method of creating long-term signatures.
It is possible that the signer creates only a basic signature, e.g. because the signer is offline. In such cases, a central verifying application can enhance and convert the basic signature into a long-term signature by embedding the timestamp and certificate status information into the signature.
This is a quite common approach. For example, one of our EU central bank customers uses this approach. So, for most signature formats it does not matter whether the signer creates the long-term signature or the central receiving or verifying application does, ADSS Server supports both options.
Long-term signatures summary
Long-term digital signatures are essential if the signed documents need to be verified months or years later.
There are many advanced digital signature standard formats for long-term verification. Ascertia ADSS Server and Go>Sign Applet are true world class, leading products in supporting advanced long-term signatures and enabling their use in many flexible ways to support the business process.
Ascertia ADSS Server also offers the underlying infrastructure services for certificate issuance, validation (CRLs, OCSP, and even XKMS and SCVP servers) as well as Time Stamp Authority server.


