This is a guest post from Erik R Van Zuuren, founder of Trustcore.EU, one of the authors of the blueprint for the Belgian Personal Identity Card Project (BelPIC) and part of key egov-supporting services at the Flemish government. Erik spoke at our 2019 Partner Event.
Just PSD2 or wider applicability?
Has eIDAS (Regulation (EU) N°910/2014 on electronic identification and trust services for electronic transactions in the internal market) changed anything?
Image source: ENISA
Will eIDAS still bring anything to the conversation moving forward, now that electronic signatures and certificate technologies have been around for a while?
Let’s take a look at experiences from Payment Services Directive 2 (PSD2) and moreover the Regulatory Technical Standard that came into force as of 14th September 2019.
Secure communications / mutual authentication
The first challenge many organisations face when interacting with third parties is how those parties can identify each other - not just technically but also with sufficient legal certainty.
Mere ’technical’ solutions like domain-validated certificates give close to no-certainty of the true identity of the party one is interacting with. Organisation-validated certificates are already a significant step in the right direction, but still do not ensure a very rigid registration process vetting the identity of the party involved. Extended Validation and Qualified Website Authentication certificates (QWACs) however do give a significant level of assurance.
If the latter two are (almost) equal, why did PSD2 put forward QWACs? There are multiple advantages. QWACs are subject to European regulation and therefore provide legal certainty on the level of assurance under which the certificates have been issued; PSD2 also legislates what quality/security/compliance requirements the issuing Qualified Trust Service Provider has to adhere to and the obligation to act (suspend/revoke corresponding certificates) if conditions change.
As a result, when two parties need to establish secure communications QWACs (especially when enriched with useful attributes like a ‘specific identifier’ or “role-information” like in PSD2) provide a solid foundation both technically and legally for parties to build upon.
Image source: ENISA
Transaction authenticity, integrity and non-repudiation
Secure communication is one thing but, when interacting with other parties authenticity, integrity and non-repudiation are often also required - and not only in the financial sector. Legal certainty is key so simple secure communication is often not enough. Often a signature or seal is needed on a transaction to provide authenticity, integrity and non-repudiation. However, like with secure communication, just using certificates and some technical signing/sealing is often not enough as it does not provide technical certainty.
This is where eIDAS demonstrates its value once again as it provides a clear legal framework, as well as a clear set of standards for Qualified Seals including standards on registration/issuance and obligations for the subscriber and issuing Qualified Trust Service Provider. 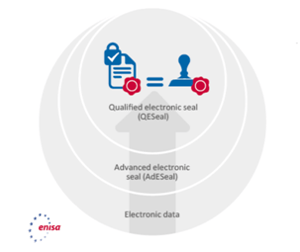
Image source: ENISA
As a result, a relying party receiving a Q-eSealed transaction can almost rely on it as if the transaction were signed by the CEO of the originating entity (note: in Belgium this is even written like that in the law).
PSD2 has however found that specific profiles were required as to be able to inject a ‘specific identifier’ and/or ‘role information’ to the certificates to enable easier consumption by the relying parties.
The same scheme could easily apply in other sectors. For example, the company’s VAT-numbers could be included as standard in the certificate and/or role-information could be added or made available in an authoritative source for that sector.
As a result, when two parties need to exchange legally certain transactions, this ‘recipe’ could enable legally certain transactions between parties (if not covered explicitly by law, then at least by mutual contract).
eIdentities and SCA
eIDAS also covered the issue of eIdentities and more importantly the topic of assurance levels of the eIdentities’ “onboarded/verified identity”. So, in the area of user, customer and business partner identification, it provides a clear and certain trust frame for schemes and parties to start from when interacting with other ‘identities’.
In government services this protects data by only allowing access if the user is identified at a sufficient assurance level. In the financial sector there are currently discussions on what level of assurance is needed in customer onboarding to allow access to which service.
One thing however should not be misinterpreted: eIdentification has nothing to do with strong authentication. A low assurance identity can use strong authentication methods or a high assurance identity can perform a weak authentication.
One could however issue strong authentication means (as defined under PSD2) or e-signing certificates (as defined under eIDAS) using rigid issuance processes to users/customers and as a result identify and authenticate users within a legally certain framework.
Consent in all its dimensions
Consent is a buzzword one hears all over the place these days. User consent for marketing and GDPR purposes is one example, while consent for a third party to access your bank account under PSD2 is another. Again, here eIDAS provides some useful elements to obtain legal certainty.
Image source: ENISA
Depending on the level of consent required in the specific business case, one can suffice with a ‘high assurance‘ identity doing a strong authentication to confirm his/her consent OR one could request the user to electronically sign a consent form. In addition and if required this ‘consent’ can be timestamped as to ensure the moment of approval is undeniable.
Transactions-approvals
When a user wants to conduct a transaction such as approve a payment, their approval is required. Again, here eIDAS can come to the rescue.
Depending on the level of approval required in the specific business case, like in the case of consent, one can suffice with a ‘high assurance’ identity doing a strong authentication to confirm his/her approval OR one could request the user to electronically sign the transaction. 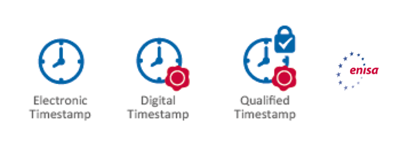
Image source: ENISA
Also here, eIDAS ensures there is a clear legal framework of how this must be done and what the corresponding legal certainty will be. In addition and if required, this approval can be timestamped to ensure the moment of approval is undeniable.
Conclusion
eIDAS has laid down a very useful framework all parties can refer to.
Subscribers/users know or should know what the (legal) value is of what they are doing. Relying Parties know what certainty they can(not) get in context of the described features and functionalities. And what is vital to support this ‘trusted’ interaction: that Qualified Trust Service Providers that enable the described scenarios are held to clear regulation and corresponding standards ensuring a high level of certainty and trustworthiness for the overall ecosystem.
So, stop thinking about eIDAS as a technical framework. It is a formidable legal trust-anchor for the digital age.
(All images sourced from ENISA and full report is available to view here)


